AWS Data Protection Overview
With the accelerating adoption of AWS as the next generation data processing platform, it is imperative that organizations deploy the appropriate level of security to manage external and internal threats without impacting user experiences. We recommend the following best practices for managing external and internal threats.
External Threat Management
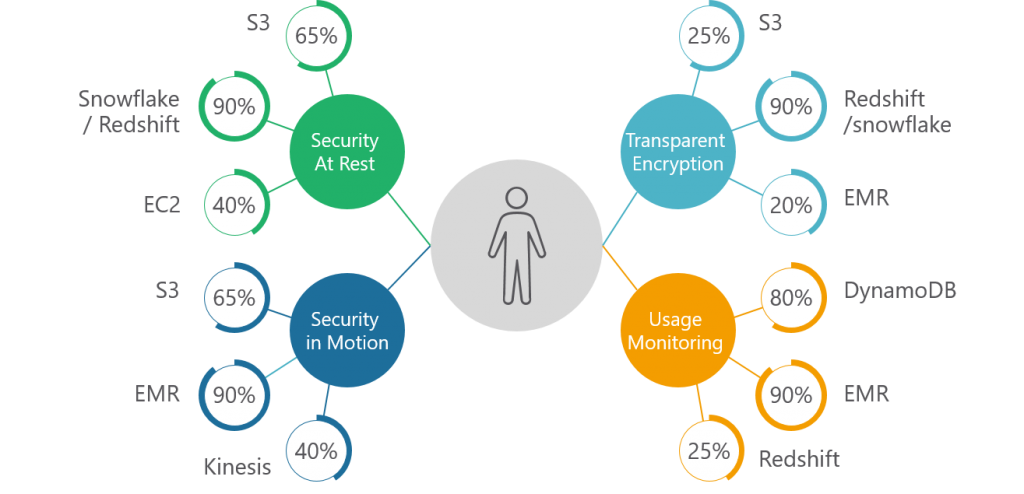
- Encrypt data files using server side or client side technology prior to uploading them AWS
- Encrypt AWS data sources at rest
- Encrypt Connection between data source and client applications
Internal Threat Management
- Identify and encrypt PII and PHI data fields prior to uploading the data files to AWS
- Preserve format and maintain referential integrity when encrypting data fields
- Enable on-the-fly decryption for the privileged AWS users and applications
- Monitor and record data usage by user and applications
- Flag anomalous user activity in real time